Your organization may have embraced cloud computing for its numerous advantages, such as flexibility, scalability, and cost-efficiency. However, it is essential to prioritize cybersecurity when it comes to your cloud infrastructure. Data breaches, intellectual property theft, and compromise of trade secrets are still potential risks in the cloud. Therefore, it is crucial to implement effective security measures to protect your critical systems and data.
What is Infrastructure Security in Cloud Computing?
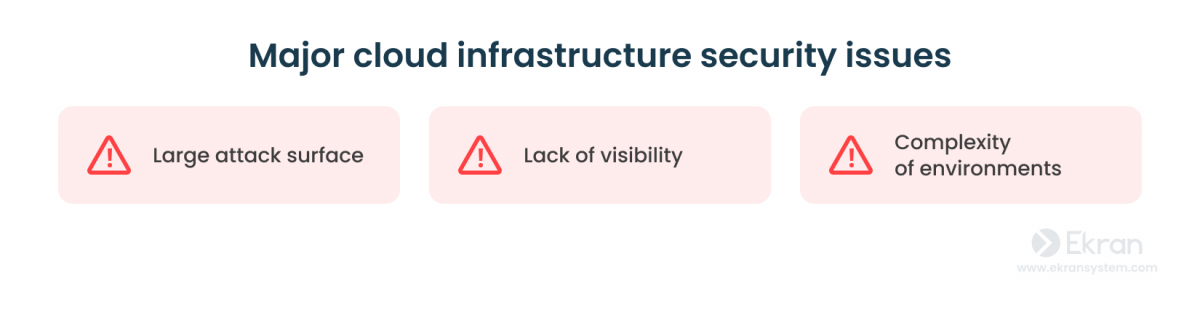
Cloud security encompasses various controls, procedures, and technologies designed to safeguard critical systems and data in cloud environments. To understand the vulnerabilities of the cloud environment, let’s take a look at its main security challenges:
Bạn đang xem: Cloud Infrastructure Security: 7 Best Practices to Secure Your Sensitive Data
- Large attack surface: It may be difficult to define the boundaries of a company’s cloud environment, leaving systems and data susceptible to attacks from multiple angles, including personal devices, unauthorized third-party applications, and public networks.
- Lack of visibility: Cloud providers often have complete control over the cloud infrastructure, making it challenging for organizations to identify and protect their assets. Additionally, tracking employee activity within the cloud can be challenging.
- Complexity of environments: Organizations may opt for complex multi-cloud and hybrid environments, which require a holistic approach to cybersecurity. Choosing the right cybersecurity tools that work seamlessly across different environments can be a challenge.
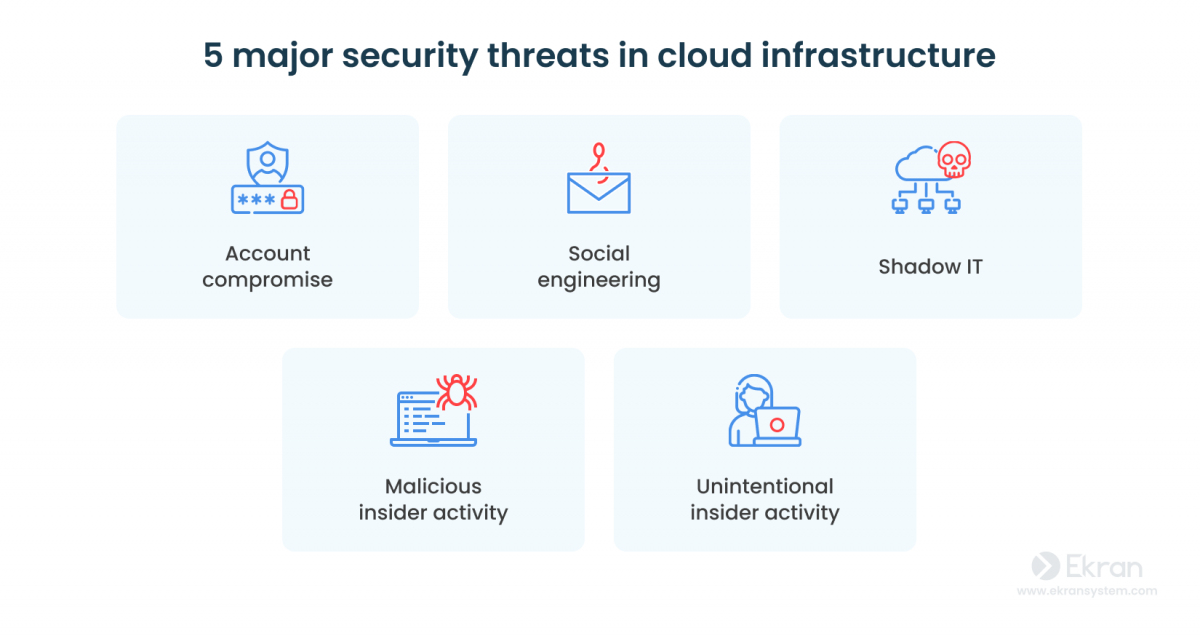
5 Major Security Threats in Cloud Infrastructure
When it comes to protecting sensitive data in the cloud, it is crucial to address the following cybersecurity threats:
Account compromise
Cyberattackers can gain access to sensitive data by taking over employee, privileged user, or third-party accounts within your organization’s cloud environment. Compromised accounts can be used to access systems, trick users into disclosing sensitive information, or carry out further malicious actions. Account compromise accounts for 15% of all cloud security incidents.
Social engineering
Cyberattackers can deceive employees into providing access to critical systems and data using techniques like phishing. Phishing involves luring victims into disclosing sensitive information through seemingly trustworthy emails. This can lead to compromised accounts and the potential installation of malware.
Shadow IT
Unauthorized cloud applications and services used by employees pose significant cybersecurity risks. These unapproved software may have extensive access rights within your cloud infrastructure, allowing cybercriminals to exploit vulnerabilities and exfiltrate sensitive data.
Unintentional insider activity
Employees’ lack of cybersecurity awareness can lead to unintentional data breaches, account compromise, and vulnerability exploits. Careless actions, such as poor password practices and sharing information via unauthorized cloud applications, can pose security risks.
Malicious insider activity
Insider threats exist in both cloud and on-premises environments. Malicious insiders may have various motives, such as industrial espionage, personal gain, or seeking revenge. Detecting and distinguishing their malicious activity from regular behavior can be challenging.
Now that you understand the key security threats in cloud infrastructure, let’s explore seven best practices to ensure data protection in your cloud environment.
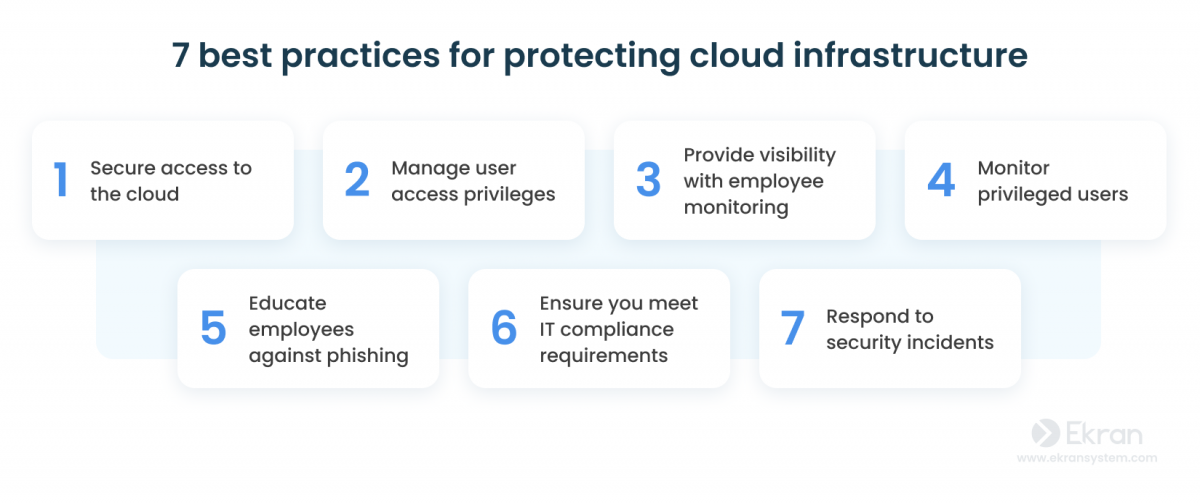
7 Cloud Security Best Practices to Protect Sensitive Data
Implementing effective cloud security measures involves a combination of cybersecurity strategies, processes, and solutions. Here are seven best practices to protect your cloud infrastructure and sensitive data:
1. Secure access to the cloud
Xem thêm : How To Customize Your Windows 10 Desktop
While cloud providers offer security measures, you are responsible for securing user accounts and access to sensitive data. Enhance password management practices in your organization by implementing password policies, such as using complex passwords and regular password rotation. Consider utilizing a centralized password management solution to streamline security.
Ekran System is a comprehensive insider threat risk management platform that can automate password management, securely store passwords, and provide two-factor authentication (2FA) for a zero-trust approach.
2. Manage user access privileges
Regularly reassess and revoke user access permissions to limit potential risks. Follow the principle of least privilege, granting users access only to the data necessary for their roles. Implement clear onboarding and offboarding procedures to control account privileges effectively.
Ekran System offers privileged access management (PAM) capabilities to granularly manage user access privileges and enforce the principle of least privilege within your cloud infrastructure.
3. Provide visibility with employee monitoring
Enhance transparency and security in your cloud infrastructure by monitoring employee activity. Monitoring can help detect early signs of account compromise or insider threats. Unusual login locations or non-working hour activities can indicate a potential breach.
Ekran System allows you to monitor and record employee activity, search for specific session details, and detect anomalies using user and entity behavior analytics (UEBA).
4. Monitor privileged users
Keep track of privileged users, such as system administrators and top management, who have extensive access to sensitive data. Establish continuous activity monitoring for privileged accounts to detect and respond to potential threats promptly.
Ekran System provides privileged user activity monitoring and access management capabilities to secure your cloud infrastructure.
5. Educate employees against phishing
Raise awareness among your employees about phishing attacks and social engineering techniques. Regular cybersecurity training and simulated phishing attacks can help employees recognize and avoid potential threats.
Ekran System can assist in protecting against phishing attacks by allowing you to analyze employee behavior during simulated attacks and detect any unauthorized activities.
6. Ensure you meet IT compliance requirements
Ensure your cloud infrastructure complies with relevant cybersecurity standards, laws, and regulations. Identify the requirements specific to your industry and organization and implement the necessary security controls and tools.
Ekran System aids in meeting compliance requirements, including GDPR, FISMA, NIST, GLBA, ISO, HIPPA, SWIFT, PCI, and SOX.
7. Efficiently respond to security incidents
Develop an incident response plan to detect, contain, and eradicate cybersecurity threats effectively. Timely response can minimize the extent of damage. Utilize user activity alerts and incident response capabilities to detect and respond to incidents in your cloud infrastructure.
Xem thêm : 5 Best Ways To Clear RAM on Android
Ekran System enables automated detection of suspicious activity and provides incident response features to help you mitigate cybersecurity incidents.
Implementing these best practices will help protect your cloud infrastructure and sensitive data from potential cybersecurity incidents. Remember, securing your cloud environment is an ongoing process that requires continuous monitoring and adaptation to emerging threats. For comprehensive security solutions, consider integrating Ekran System into your cloud infrastructure.
Frequently Asked Questions
Q: How can I secure access to my organization’s cloud infrastructure?
A: Secure access to the cloud by implementing strong password management practices, such as using complex passwords, regular password rotation, and centralized password management solutions. Additionally, consider implementing two-factor authentication (2FA) to enhance security.
Q: What is the principle of least privilege, and why is it important?
A: The principle of least privilege states that users should only have access to the data necessary for their roles. Granting minimal access privileges reduces the risk of compromised accounts leading to unauthorized access to critical data.
Q: How can employee monitoring improve cloud infrastructure security?
A: Employee monitoring provides visibility into user activity within the cloud infrastructure, allowing organizations to detect early signs of account compromise or insider threats. Monitoring can help identify abnormal activity and take timely actions to mitigate risks.
Q: What is the importance of meeting IT compliance requirements in the cloud?
A: Compliance with cybersecurity standards, laws, and regulations ensures the protection of sensitive data and helps organizations avoid significant financial penalties in the event of a data breach. It is crucial to understand and adhere to the compliance requirements specific to your industry.
Q: Why is an incident response plan important for cloud security?
A: An incident response plan is crucial to detect, contain, and eradicate cybersecurity threats quickly. A well-defined plan with assigned roles and procedures enhances the organization’s ability to respond effectively to security incidents, minimizing potential damage.
Conclusion
Securing your cloud infrastructure requires addressing potential vulnerabilities and implementing robust security practices. By following these seven best practices, you can protect your organization’s sensitive data and mitigate cybersecurity risks effectively.
Remember, cloud security is an ongoing effort, and regularly reassessing and adapting your security measures is essential. For comprehensive insider threat risk management and cloud security solutions, consider integrating Ekran System into your cloud infrastructure.
Nguồn: https://eireview.org
Danh mục: Technology