Humans have an inherent need to communicate with each other. It’s how we form relationships, seek help in times of need, and navigate through life. However, it’s also true that humans can use communication to harm and exploit others. This dual nature of communication has led to the development of encrypted radios—communication devices that ensure privacy and security.
The Value of Encryption
Encryption is a vital aspect of communication security. It involves the use of mathematical algorithms to convert readable information into an unreadable format. This ensures that only authorized recipients can access and understand the message. Encryption is widely used by various entities, including governments, businesses, and individuals, to protect sensitive information from unauthorized access.
Encryption has numerous applications, such as protecting classified information, trade secrets, and personal data. It can be used to secure files, emails, chat histories, and even mobile devices. By encrypting data, individuals and organizations can mitigate the risk of identity theft, cyber attacks, and other security breaches.
Legality and Restrictions
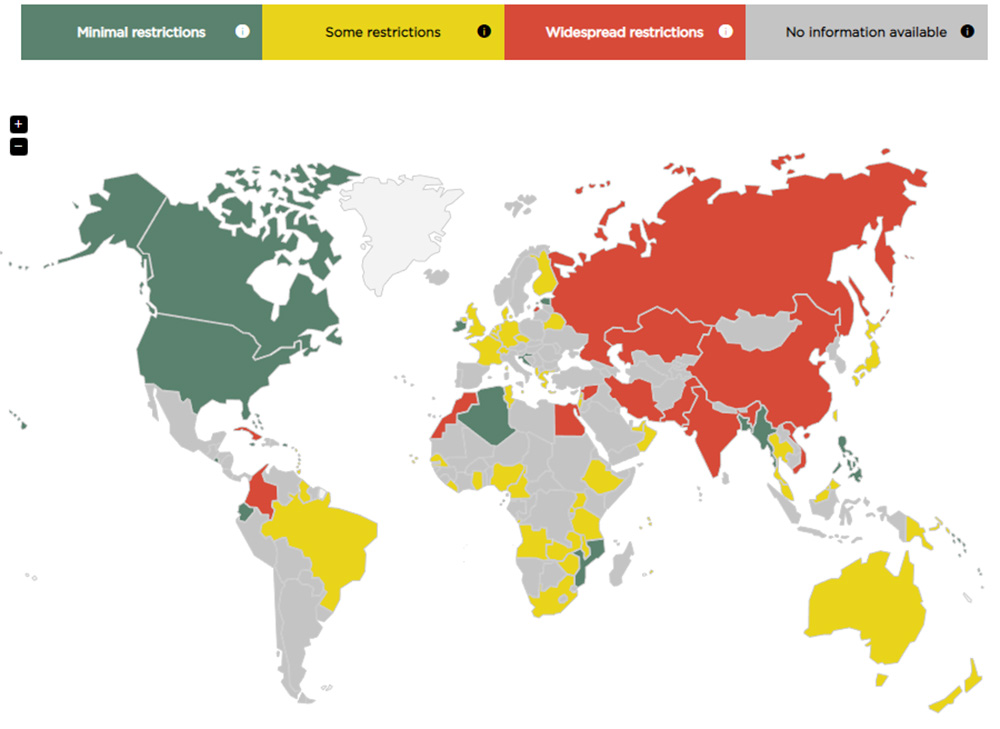
While encryption provides a strong layer of security, its use is often tightly controlled by governments. Different countries have varying laws and regulations regarding the use of encryption technology. Some nations impose widespread restrictions, while others have minimal restrictions or even allow encryption without limitations.
It’s important to be aware of the legal implications of using encrypted radios in your country. For example, in the United States, amateur radio users are prohibited from transmitting messages encoded to obscure their meaning. However, exemptions exist for military, law enforcement, and emergency services, as well as businesses that obtain the necessary licenses.
P25 Radio Standard
The Project 25 (P25) radio standard was developed to facilitate interoperability among emergency response agencies. It enables different agencies and jurisdictions to communicate effectively during emergencies. P25 radios are digital two-way radios that can also communicate with analog radios. They are widely used by police, fire, ambulance, and other emergency rescue services.
P25 radios can operate without encryption, allowing anyone with a compatible radio to listen and respond. However, for higher-security applications, P25 radios can be configured to use encryption. The encryption options include the 56-bit Data Encryption Standard (DES) and the more secure 256-bit Advanced Encryption Standard (AES).
DES and AES Encryption
The Data Encryption Standard (DES) was developed in the late 1970s and was widely used for secure communication. However, advances in computing power made it possible to break DES through brute force attacks. As a result, the more secure Advanced Encryption Standard (AES) was developed and became the preferred encryption algorithm.
AES is available in different key lengths, including 128-bit, 192-bit, and the most secure, 256-bit. AES-256 is considered virtually unbreakable when implemented correctly. It is widely used in various applications, including file encryption, secure communication protocols, and data protection. AES-256 is the encryption standard approved by the National Security Agency (NSA) for top-secret data storage.
Encrypted Radio Vulnerabilities
Xem thêm : Best Multi-Computer Cloud Backup and Storage
While encryption provides strong protection, there are other vulnerabilities to consider when using encrypted radios.
Radio Direction Finding (RDF): RDF is a technique used to locate the source of a radio transmission. It can be used to track down transmitters and interfere with communication. Avoiding predictable patterns and locations can help mitigate the risk of RDF detection.
Hardware Interception: Encryption can be bypassed if a radio with the encryption key or the programming computer is captured. Organizations often use Over-The-Air Rekeying (OTAR) to periodically update encryption keys and prevent unauthorized access.
Jamming: Jamming attacks can disrupt or block encrypted radio transmissions. Selective jamming can force radios to switch to unencrypted mode, compromising security. Protecting against jamming attacks is challenging, and it often requires physical countermeasures or changing communication frequencies.
Closing Thoughts
Understanding the basics of encrypted radios is crucial before considering their use. Encryption provides a vital layer of security, but it’s important to be aware of legal restrictions and potential vulnerabilities. Encrypted radios can serve as a lifeline during emergencies or when privacy is paramount. By being prepared and knowledgeable, individuals and organizations can enhance their communication security and protect sensitive information.
Frequently Asked Questions
- Q: Are encrypted radios legal? A: The legality of encrypted radios depends on the laws of the country in which they are used. It’s essential to research and understand the relevant laws and regulations.
- Q: Can civilians get encrypted radios? A: In many countries, encrypted radios are restricted to certain authorized entities such as the military, law enforcement, and emergency services. Civilian access to encrypted radios may be limited or prohibited.
- Q: Is it illegal to decrypt police radio? A: Intercepting and divulging police radio communications is generally illegal in many jurisdictions, including the United States. It is essential to comply with regulations and laws regarding radio communications.
This article was brought to you by Eireview – Extractive Industries Review. Don’t forget to subscribe to our free newsletter for more informative content.
Nguồn: https://eireview.org
Danh mục: Technology