What is “We Noticed a Login from a Device You Don’t Usually Use”?
“We noticed a login from a device you don’t usually use” refers to an email spam campaign – a mass-scale operation during which thousands of deceptive emails are sent. The letters distributed through this campaign are disguised as notifications concerning a suspicious device having been used to sign into the recipients’ email accounts.
Bạn đang xem: How to Spot Scams Like “We Noticed a Login from a Device You Don’t Usually Use”
The goal of these scam letters is to trick users into exposing their email account log-in credentials (i.e., email addresses/ usernames and corresponding passwords) by attempting to log in via a phishing website.
“We Noticed a Login from a Device You Don’t Usually Use” Scam Email in Detail
Xem thêm : 12 Online Scam Protection Tips To Keep Yourself Secure
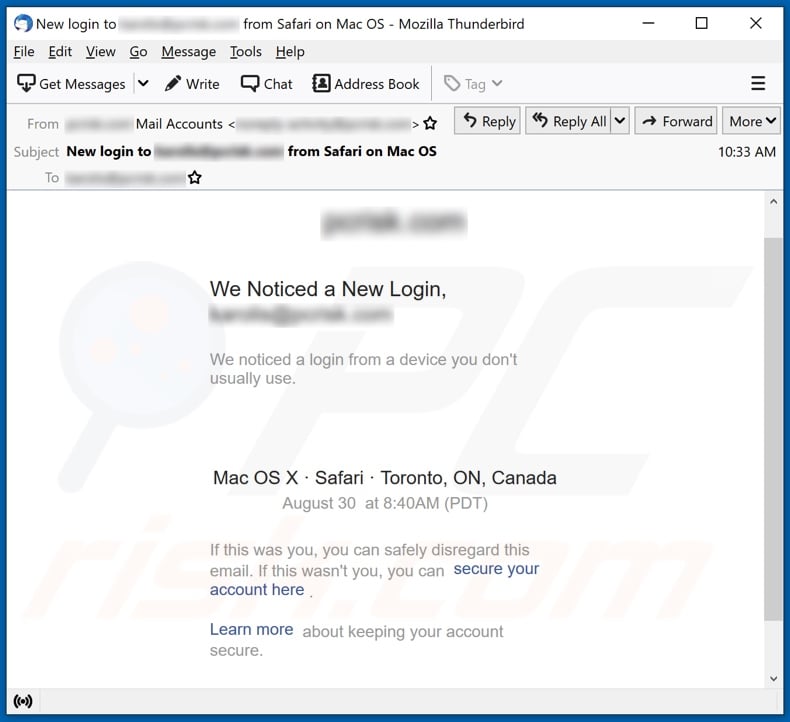
The “We noticed a login from a device you don’t usually use” scam emails (subject/title “New login to [recipient’s email address] from Safari on Mac OS”; may vary) inform about a dubious log-in through a previously unused device. The fake notifications then go on to list details of the alleged sign-in to the recipient’s email account.
The letters instruct to disregard them if it was indeed the recipient who had logged into their account. However, if it was not them – the emails tell the recipient to click “secure your account here”.
Despite how legitimate these emails may seem, it must be emphasized that they are fake. Therefore, no unauthorized access to the recipients’ accounts has occurred. Furthermore, the link provided in these letters leads to a phishing website disguised as an email account sign-in page.
Sites of this type operate by recording the data entered into them. Therefore, recipients may have their email accounts stolen by attempting to sign in through the website promoted by the “We noticed a login from a device you don’t usually use” scam letters.
Xem thêm : Top eBay Inventory Management Tools
Scammers target emails as they are typically connected with (e.g., used to register) other accounts, platforms, services, and so on. Therefore, through stolen email accounts – cyber criminals may gain access/control over content associated with them.
To elaborate on how this can be abused, communication accounts (e.g., emails, social networking, social media, messengers, etc.) can be used to ask the contacts/friends for loans – under the guise of the genuine owner. Alternatively, these platforms can be employed to proliferate malware by sharing malicious files or links.
Finance-related accounts (e.g., online banking, money transferring, e-commerce, digital wallets, etc.) can be used to make fraudulent transactions and/or online purchases. In summary, by trusting the “We noticed a login from a device you don’t usually use” scam emails, users can experience severe privacy issues, financial losses, and identity theft.
Threat Summary:
- Name: We noticed a login from a device you don’t usually use Email Scam
- Threat Type: Phishing, Scam, Social Engineering, Fraud
- Fake Claim: Scam emails claim that a previously unused device has logged into the recipients’ email accounts
- Symptoms: Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer.
- Distribution methods: Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled d
Nguồn: https://eireview.org
Danh mục: Technology