Gebhard’s diary entry “Brute Forcing Simple Archive Passwords” has inspired me to enhance my zipdump.py tool with brute-force password cracking capabilities. In this article, I will walk you through the process of using zipdump with the new brute-force attack mode.
Bạn đang xem: Internet Storm Center
How to Use Zipdump for Brute-Force Password Cracking
Years ago, I added dictionary password cracking to zipdump.py, a tool designed for analyzing ZIP files. With the latest version, I have made it even more versatile by introducing a brute-force attack mode.
To initiate a zipdump dictionary attack, you can use the options -P (passwordfile) or -passwordfilestop. You have the option to provide a text file containing passwords to try (such as rockyou), or you can simply use the file name “.” to utilize the built-in password list (John-the-Ripper’s public domain password list).
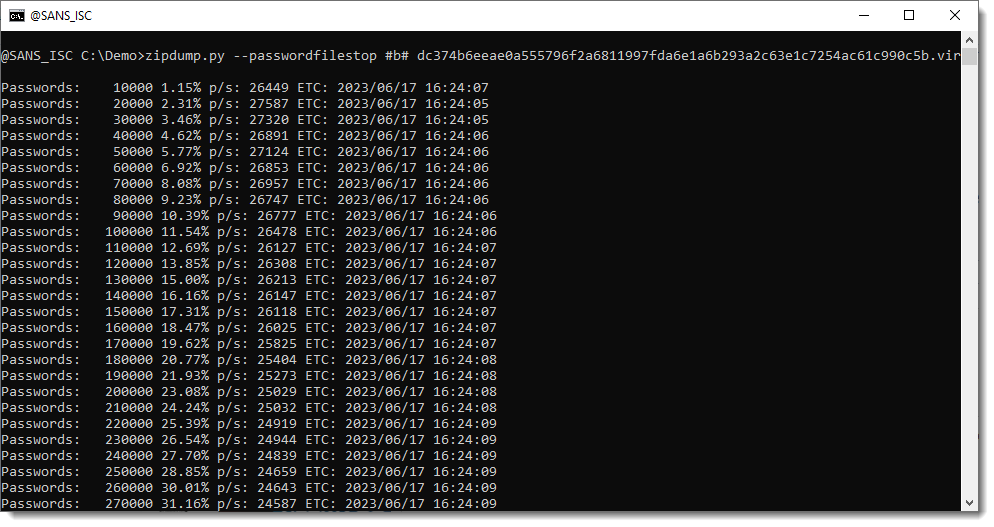
Alternatively, you can start the brute-force attack mode by using the special filename: #b#. This mode allows zipdump to generate password guesses ranging from 1 to 3 characters long, using a combination of uppercase and lowercase ASCII letters, digits, punctuation characters, and the space character.
The brute-force attack runs at an impressive rate of almost 25,000 password guesses per second on the tested laptop. However, it’s important to note that the recovery of passwords is not guaranteed.
Customizing the Brute-Force Attack
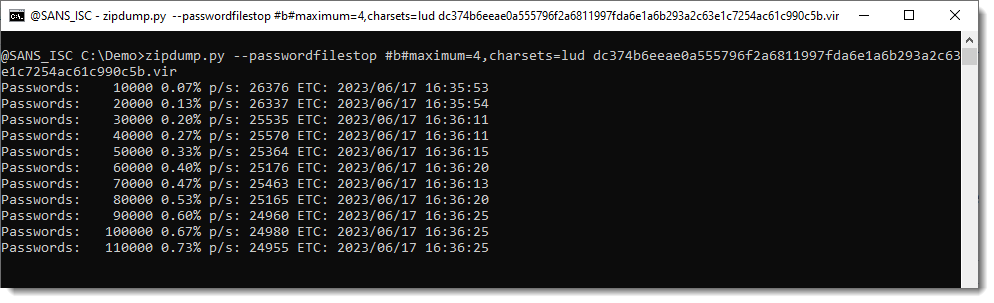
If you have specific information about the password, such as its length and character set, you can further customize the brute-force attack. Let’s consider an example where Gebhard discovered that the password is 4 characters long and consists of uppercase letters and digits.
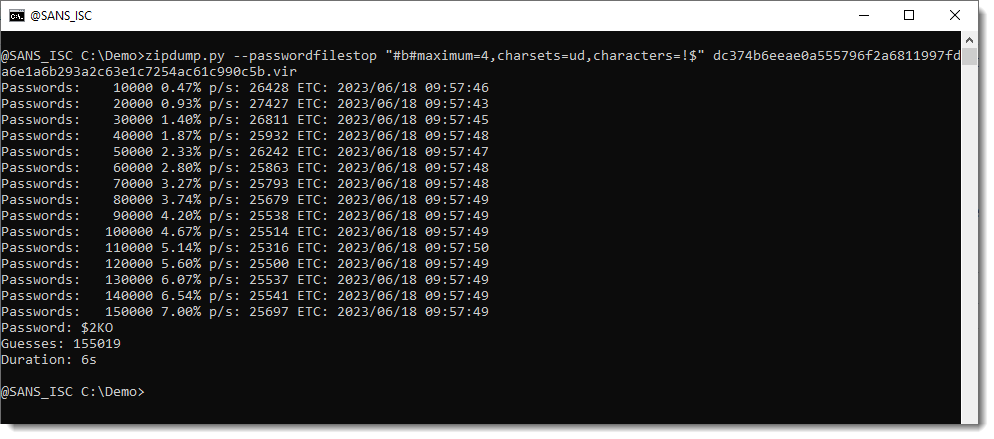
To perform this specific attack, you can use the parameters maximum=4,charsets=lud. This configuration initiates a brute-force attack targeting passwords consisting of uppercase and lowercase letters and digits, with lengths ranging from 1 to 4 characters.
Xem thêm : Community
In this case, it took approximately 505 seconds to recover the password: X353.
Limitations and Future Improvements
It’s important to note that zipdump only handles ZIP files and does not support all archive types like Gebhard’s shell script. Additionally, for ZIP files encrypted with AES (such as those obtained from Malware Bazaar), the cracking process is significantly slower, with less than 2,000 password guesses per second on the same laptop.
Another aspect to consider is that zipdump may generate false positives. While it may be possible to open a ZIP file with a guessed password through the zipfile/pyzipper API, errors may occur when attempting to fully access the contents of the file.
I am aware of this issue and will address it in an upcoming version of zipdump.
Frequently Asked Questions
Q: Is zipdump suitable for cracking complex passwords?
A: While zipdump’s dictionary and brute-force password cracking feature can handle simple or popular passwords, for more complex passwords, it is recommended to use tools like hashcat.
Conclusion
Zipdump with its new brute-force attack mode is a powerful tool that allows users to analyze and crack ZIP file passwords. By customizing attack parameters, you can increase your chances of successful password recovery. However, it’s worth noting that the process may vary depending on the complexity of the password and the encryption method used. Stay tuned for future updates and improvements to zipdump.
Didier Stevens – Senior Handler, Microsoft MVP
blog.DidierStevens.com
Nguồn: https://eireview.org
Danh mục: Technology